
There are vulnerabilities that last for months and cause problems all this time. But there are others that last even longer and that is what has happened with a vulnerability in the Python programming language: more than 15 years being vulnerable and with hundreds of thousands of people affected, this language has once again been the center of attention due to a problem that never had a solution many years ago.
The security issue has been around for over a decade and has never received a patch. It has been overlooked for 15 years and it is estimated that it may have affected more than 350,000 open source repositories since it was revealed in 2007. It was now that researchers from the company Trellix (formed by the union between FireEye and McAfee ) have put the focus on this problem.
In 2007 it was disclosed and tagged as a vulnerability CVE-2007-4559. But it was never fixed and the vulnerability was considered to be of little importance. But now, according to the Trellix researchers, it would have spread across many machine learning applications. At the time, there was only one documentation update that warned developers about it and about the risk it could pose, but without seeking any solution to it…
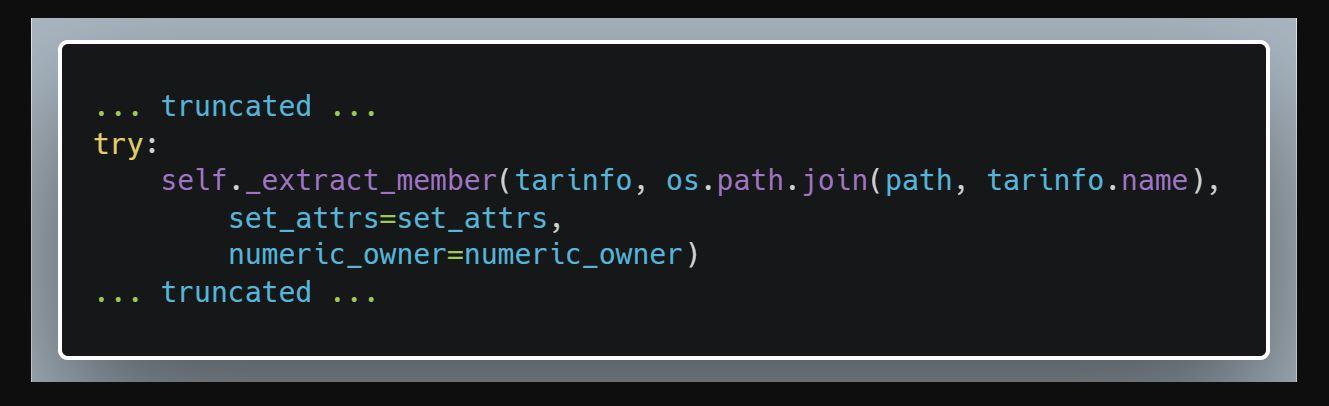
We now know that the vulnerability appears in the “extract” and “extract all” functions in the Python tarfile module. The vulnerability can be exploited with a malicious file generated with just a few lines of code, and this would allow attackers to execute arbitrary code.
More than 350,000 projects affected
The number of affected projects is 350,000 according to Trellix researchers who discovered the vulnerability and analyzed the impact. It was present in thousands of software projects, among which there were open source projects and others that were not. To do this, the researchers reviewed around 257 repositories and saw how many of them included vulnerable code. They manually checked 175 of them to see if they were affected and were able to find more than 60% of cases.
The set of samples, as explained by Bleeping Computer, served as a reference to have an estimate of all the repositories available on GitHub that had been affected, and Trellix concluded that there were more than 350,00 vulnerable repositories and many of them had been used by learning tools. automatic, automated tools based on the code of hundreds of thousands of repositories and that have the function of making an automatic completion to finish a project faster. By providing insecure code, this problem or vulnerability spreads to other projects globally.
In addition, the company has reminded that open source development tools like Python are necessary to move forward but depend on industry collaboration to protect against vulnerabilities. From Trellix they assured that they are already working on how to protect open source projects from vulnerability with a free tool that developers can use to know or to verify if their applications are vulnerable or not.