Linux has always been considered a much more secure operating system than Windows. And not because it does not have vulnerabilities (which it does, like any software), but because of its nature when it comes to controlling the permissions of users and the programs that are executed, greatly limiting what any element can do if it does not have permissions . However, just as Windows has its own administrator account, many Linux distros come with a root account enabled by default. And this can put our security in total check.
By default, a standard user of a Linux distro has very limited control over the system. In other words, he can only work within his directory and use whatever programs he has installed, as long as they don’t require elevated permissions.
If we want to install programs, or make changes to the system, we will need to have elevated permissions. And these can be achieved in two different ways. The first one, and the most used, is to invoke sudo. What this program does is allow any user on the system to execute a command with the level of security privileges of another user. It is generally used to execute commands with “root” permissions. And, the second one is to log in to the system as “root” via “su” command.
The difference between both commands is that, when we use “sudo”, we must enter the password to execute the command, but the superuser permissions disappear once the execution of the command is finished. However, with “su” we keep ourselves administrators in the terminal indefinitely, until we ourselves stop being root using the “exit” command and have our normal privileges again.
Why disable the root account
As we can see, using the root account may seem, at first glance, something more comfortable. But, in reality, it poses a significant danger to our security. In addition, it is much more comfortable to use “sudo” than “su” because, in this way, we will only have to remember one master password (that of our user) instead of also having to remember the password of the root user.
If there are multiple users logged into the system, each of them can invoke “sudo” using their own password. If this password is exposed, it will be enough to change this password and other users will not even have to know that this has happened. Conversely, if the root user’s password is exposed, in addition to compromising the entire system, it would have to be changed and shared with all other admin users using this account. And, the more users who know a password, the more likely it is to be exposed.
Prepare Linux to disable the root account
Generally, most Linux distributions allow users to use “sudo” to run, with the first user we create, tasks with elevated super-administrator permissions. However, it never hurts to check that this is possible, and that some other changes have not been made that prevent us from using it, before continuing.
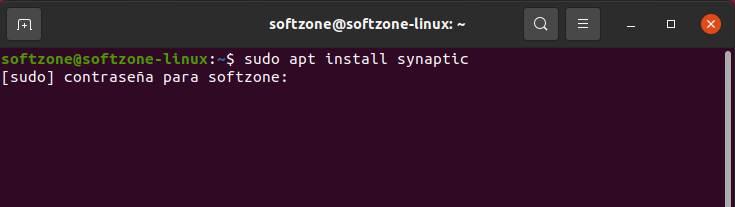
We simply have to execute a command that requires elevated permissions (such as apt) preceded by the “sudo” command and check if, indeed, our user can use this tool. Linux will ask us to enter our user’s password before executing the command with elevated privileges.
If we do not have sudo installed, first of all, we will have to install it. And for this, we will have no other option than to use “su” to carry out the task with the permissions of the root user.
And finally, if we want to limit the users who can or cannot use the “sudo” command, we can use the “visudo” tool. This tool allows us to open a copy of the “/etc/sudoers” configuration file, and it will only allow us to save the changes when it is a valid configuration.
lock root account
At this point we will have verified that, indeed, our user account can use the “sudo” command to execute tasks with elevated privileges. Then, the time has come to disable the root account of the system to prevent anyone from using it, neither for better nor for worse.
To do this, we simply have to open a terminal and execute the following command:
sudo passwd -l root
What this command does is lock the root user so that no one can use the “su” command or log in directly to a TTY using the “root” user along with their password. If we now try to run “su” on the system, we will realize that Linux does not allow us to do so. Now, our distro is a bit more secure.
Other Linux Security Tips
Although deactivating the Linux root account gives us a security plus, there are other little tricks and some configurations that we can use to make our system much more secure.
For example, one of the fundamental factors for our system to be properly protected is to make sure that it is always up to date. In addition to the programs that we have installed, we must also make sure that the Linux kernel (the Kernel) is also always up to date, as well as all the packages that are part of the operating system.
Another important point that we must take care of when protecting our Linux is to control the permissions of all users. If anything characterizes Linux, it is the great control it offers us over all this. We can configure to the millimeter, thanks to user permissions and groups, what each user, or each program, can do, and what not. Also configure the permissions of the folders, specifying who can enter them and read their data and who cannot.
One more aspect to keep in mind is to disable all unnecessary services. Normally, Linux enables a series of protocols to facilitate its remote administration, but it is very likely that we do not need them. In that case, what we have to do is disable everything that we don’t use (for example, FTP or Telnet) to prevent them from using those protocols to connect remotely to our PC.
Of course, it is also essential to ensure that we use strong passwords for all users. And, its can be with a 2FA system, much better. In this way we will ensure that hackers cannot compromise our accounts with different attack techniques and that our equipment is connected to the Internet securely.