The Play Store is the Android application store, a “safe” space from which we can download any application for our mobile device. In theory, the applications in this store are reviewed by Google so that we have that guarantee that the apps are safe and reliable and we do not take risks when downloading them from that store. However, more than once, Google’s security controls have proven to be ineffective at all. And again, the worst has happened again.
Security firm McAfee has released an advisory about a new security issue that has hit the Google app store. In total, as indicated by the security firm, 43 applications with hidden malware have been found, which in total add up to more than two and a half million installations.
The malware that hides within these applications what it does is load ads on the device when the screen is off. This is not only an annoyance for the user, but also results in a considerable drain on the battery, which can be depleted in a matter of hours. However, depending on the advertising that appears on the smartphone, it is also possible that they consume too much data from the 4G rate, and even try to trick us into carrying out a scam.

Initially, this threat has only been detected in applications related to streaming, calendars and news aggregators. And the general audience of the campaign is Korea, although it is very likely that the hackers have other campaigns in mind to infect users in other countries with similar techniques.
It is relatively easy to check if we are infected. First of all, if we have downloaded any of the apps that McAfee mentions, we are probably victims of these pirates. We can also check the battery consumption of the mobile and see which apps and processes use the most battery, especially when idle, to detect possible patterns that make us think that we are infected.
How pirates upload Android apps with malware
When an Android app developer uploads an app, Google’s AI reviews it. If everything is correct, it usually happens by the way, especially if it is an update (and not a new app). If there is even the slightest suspicion, the app is manually reviewed by the company’s own engineers to decide if it is good, and it is allowed to pass, or if it is dangerous and its publication is blocked.
So how can these things happen? Very easy. Hackers use code that can be altered remotely. In this case, through Firebase Storage or through messages sent to the app remotely. In this way, when the app is uploaded to the store, it is completely harmless. But when it is downloaded, and connected to Firebase or the hacker’s control server, the code mutates, and it becomes a malicious app.
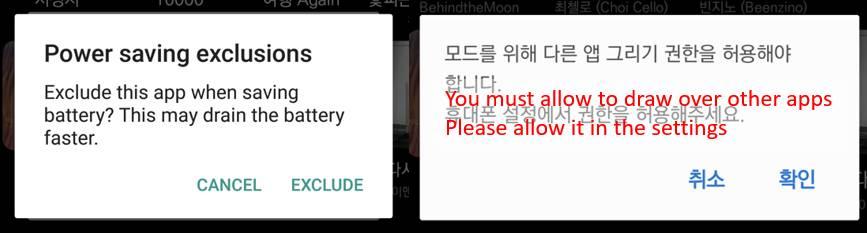
Despite this, part of the blame lies with Google, since for these types of apps to work they need very aggressive Android permissions (such as running without battery control, or showing overlapping windows, a technique used by banking Trojans). permits that, as standard, should raise suspicions when passing the store controls.