A Spanish aerospace company has been cyberattacked by Lazarus, a North Korean hacker group. To do this, they used their current campaign, “Operation Dreamjob,” which involves approaching a target through LinkedIn and participating in a fake employee recruitment process.
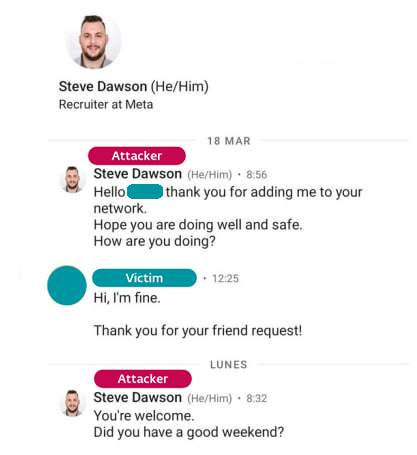
Security threats use phishing as a way to lower the protection of their potential victims. An example of this has been how a Spanish aerospace company has been hacked and it all started with a LinkedIn message from a supposed recruiter posing as a Meta employee.
Korea hacks a Spanish aerospace company
The North Korean hacking group Lazarus targeted employees of an aerospace company located in Spain. The group addressed several company employees through messages on LinkedIn, the leading social network for finding employment. Posing as a Meta recruiter, the attacker used a job offer as a decoy to attract the attention and trust of the target, a worker at the affected Spanish aerospace company.
Their goal was to hack the corporate network using a previously unknown backdoor called LightlessCan. During the supposed selection process, the victim must download some files.
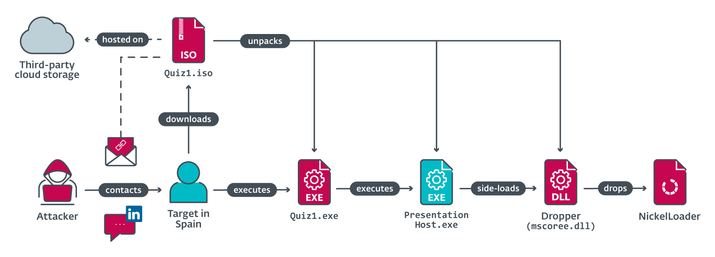
The deceived employee was reckless enough to download the file to a computer at the company he works for, thus providing the back door for the North Korean hacker group. According to ESET, who discovered this infiltration, the victim was asked to demonstrate his mastery of C++ programming by downloading some questionnaires that were shared as executables within ISO files. Once those executables were launched, an additional payload of the ISO images was silently placed on the victim’s machine via DLL sideloading (mscoree.dll) using a legitimate program (PresentationHost.exe).
The two malicious executables, Quiz1.exe and Quiz2.exe, which were delivered via the Quiz1.iso and Quiz2.iso images hosted on a third-party cloud storage platform and which upon execution release the payload. That payload is the NickelLoader malware loader, which implements two backdoors, a variant of BlindingCan with grayed-out functionality (miniBlindingCan) and LightlessCan.
Access to the corporate network
The first payload delivered to the target system is an HTTP(S) downloader named NickelLoader. The tool allows attackers to implement any desired program in the memory of the victim’s computer.
Once NickelLoader runs on the target system, attackers use it to deliver two types of Remote Access Trojans (RATs). One of these RATs is already known to be part of the Lazarus toolkit, specifically a variant of the BlindingCan backdoor. Additionally, the attackers publicly introduced a previously undocumented RAT, which they called LightlessCan.
ESET says LightlessCan is a successor to BlindingCan, based on the source code and similarities in command order, featuring a more sophisticated code structure, different indexing and improved functionality.
The sampled version of the attack on the Spanish aerospace organization is 1.0, which supports 43 commands. However, ESET says there are 25 other commands in the code that have not yet been implemented. The malware replicates many native Windows commands such as ping, ipconfig, netstant, mkdir, schstasks, systeminfo, etc., so it can execute them without appearing in the system console for better stealth from real-time monitoring tools.













