Criminals are constantly exploring all the methods that exist to steal our data and extract our passwords. One of the latest scams detected occurs via email and we can differentiate it in a very simple way, by the subject. We tell you.
The digitization It has brought a large number of benefits to the citizens and companies of our country. However, as organized criminal groups have discovered the possibilities that provides the online channel, There are many who are constantly exploring all the avenues that exist to try to gain the trust of their victims and, subsequently, steal all our data.
And this is precisely what happens with one of the latest scams detected. Although, in this case, it seems that its objective is not private users, but the companies. Regardless of their size, it is common that in this type of environment we always find invoices to suppliers that have already been paid or are pending payment. And it is precisely this last case that foreign lovers try to take advantage of to try to introduce a type of malware hidden behind an attachment.
Beware of late payments
The emails that have been detected always have the same issue or, at least, a very similar one: late payments, pending invoices, remaining invoice, etc. They usually go to corporate email accounts from profiles that have been previously selected for occupying certain job positions: people who work in administration and accounting, operations or finance departments.
The message we receive can have different variants. However, in all of them they tell us that we have a fpending action with them and that we proceed to liquidate it immediately, inviting us to open the attachment found in the email. In which, in theory, the invoice is located. In some cases, in fact, they state that if the situation is not resolved in a short period of time, they will take legal measures about it and will file a complaint. In this way, try to pressure the recipient of the email as much as possible to create a false sense of urgency and not check if it is, in fact, a supplier with whom you have worked at some point.
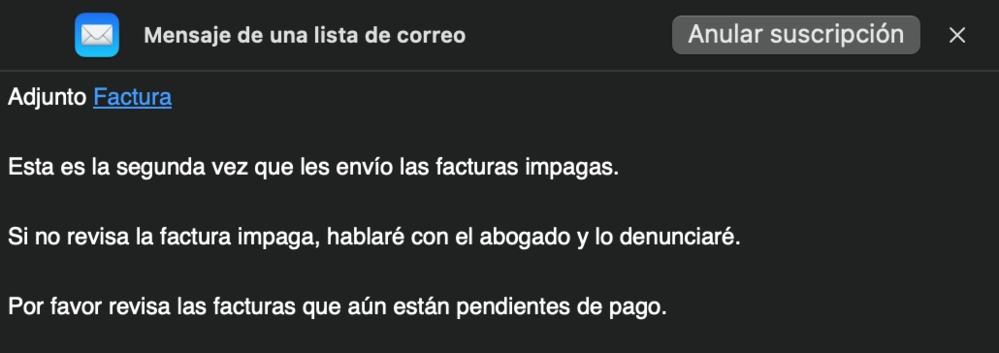
The attached file
As we have already anticipated, in the attached file the email key is found. Regardless of its nomenclature, we must avoid opening it at all costs. Since inside there is a type of malware that, when executed, tries to access as much data as possible in order to ultimately market it and include it in possible new similar or any other type of attacks.
If we receive one of these emails, the first thing we have to do is try to avoid opening them. If we do so, we should not interact with the attached file. And, if we do, we must notify the relevant authorities and, in addition, proceed to change all passwords, in addition to deleting the email in question. Faced with any similar action, we must always try to be patient and avoid opening emails from senders that we do not know and that may be suspicious.













