When it comes to the security of our devices, installing malicious software without us realizing it is a very serious mistake. Hence, the attackers try to sneak these programs into us in order to access our equipment and data, as is happening in the case that we will show you on Android.
This is something that of course is extensible to both our desktop computers and mobile devices. Both modalities are almost constantly exposed to possible attacks and security breaches. In this case we want to focus on the mobile devices that most of you carry constantly in your pocket. Specifically, we will talk about a series of malicious applications that precisely, a priori, their purpose is to improve our security.
We tell you all this because a series of malicious authenticators have been discovered that can lead us to download them to improve our security, and in reality we achieve the opposite. A few days ago, a set of apps available in the official Apple store that posed as authenticators and were actually malicious apps was made public. Well, now it is known that something very similar is happening in the official Google store for its Android system.
Given the huge market penetration of Google’s mobile operating system, this represents a serious danger. Furthermore, all this is accentuated by the fact that these malicious applications are found in the official store of the system, Google Play. We must keep in mind that a priori the main objective of real authenticators is to improve our security.
Don’t trust any authenticator on Android
These add a second layer to the authentication process, normally generating temporary QR codes that users must enter in the login process of the platforms that we register here.
Furthermore, these apps are also used for other security related tasks. Of course, when choosing a specific one we have a wide range of software of this type to install on our mobile. This is something that we find in both the official iOS and Android stores.
In short, authenticator apps prevent brute force attacks against accounts and password leaks. What’s more, some large technology companies such as Apple or Google have their own software solutions with these characteristics. It is difficult to access a user’s authenticator, since access to the device is required. But if the app itself is already malicious, the attack is simplified.
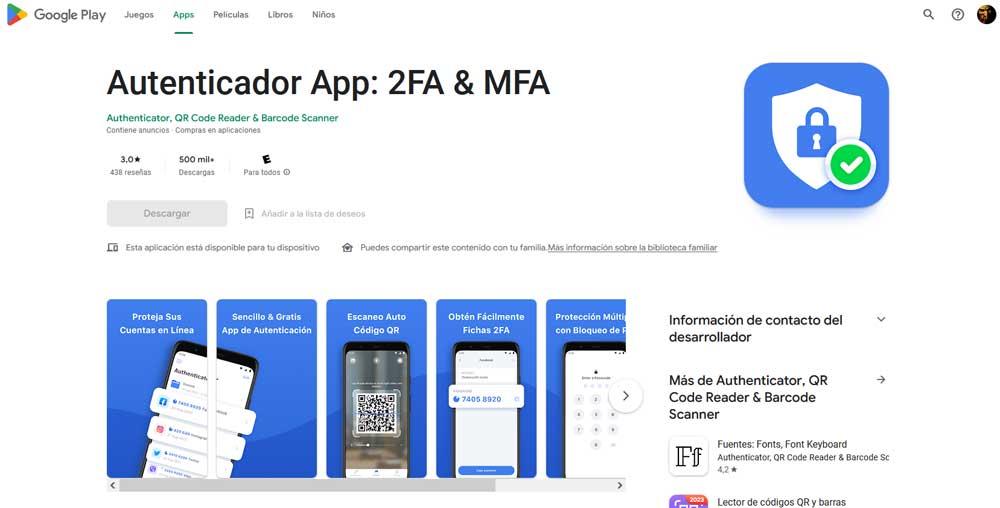
Among the malicious applications of this type that have been detected in the official Google store, a special mention has been made about one in particular, Authenticator App: 2FA & MFA. The reason for this is that it had more than half a million downloads on Google Play and an average score of 3.8.
At first it seems that the particular application works as a normal authenticator to generate one-time codes. But in the background it sends these generated QR codes to a remote server. With these codes in their possession, attackers can generate new ones for the linked service at any time. Although they also need the user’s master password and username, they disable the second layer of defense, so we should not use this software in any case.












