When launching our favorite web browser and starting to move around the internet, one section that we take into account is that related to privacy and security. This is something that is extended when using social platforms such as Twitter. Well, this is the novelty that has just been launched for the Tor network right now, let’s see how to access it.
Many of you may already be aware of the Tor project focused on providing us with an extra level of privacy when we move around the internet. Well, right now we can confirm that Twitter has launched its .onion website for the aforementioned Tor project. With this, what we really want to tell you is that from this moment on, users who normally use the Tor network will be able to access the social network through their own dedicated portal. Next, we will show you how to achieve it.
Of course, we must take into consideration that access to the Tor network is available in several ways. On the one hand, users have the possibility to download the Tor Browser web browser which is based on Firefox ESR. From here we will be able to browse any website, including .onion sites. Similarly, other programs of this type, among which we can mention Brave, also support the Tor network.
How to access and use Twitter with Tor Browser
We must know that the aforementioned Tor Browser is currently available for both desktop and Android operating systems. One of the main advantages that it offers us is that it uses encryption and other privacy and security functions to protect the anonymity of users. All this is achieved by routing the connection through a series of network nodes instead of connecting directly with the visited websites.
Therefore, to connect to Twitter through this private network, the first thing we do is download tor browser. We can also opt for the Brave browser for all of this. These two programs allow us to move through the aforementioned Tor network and therefore load .onion sites. Keep in mind that these two browsers are installed like any other program in our operating system.
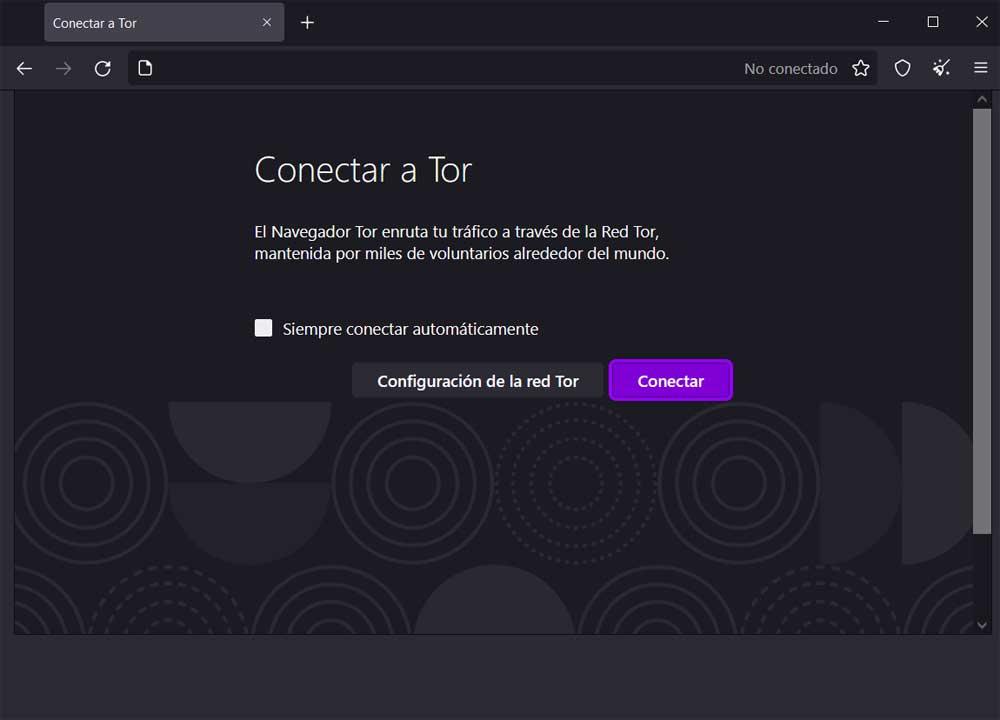
If we do not opt for the first, we find that when we start the browser we have the possibility of configuring the program or directly connecting to the Tor network. To do this, all we have to do is click on the Connect button to move around the internet using the private network. Therefore, after that, to be able to access the Twitter social network from it, we can do it through this link. This will give us direct access to the personal account of the blue bird’s social network. We will only have to enter our credentials in a conventional way.
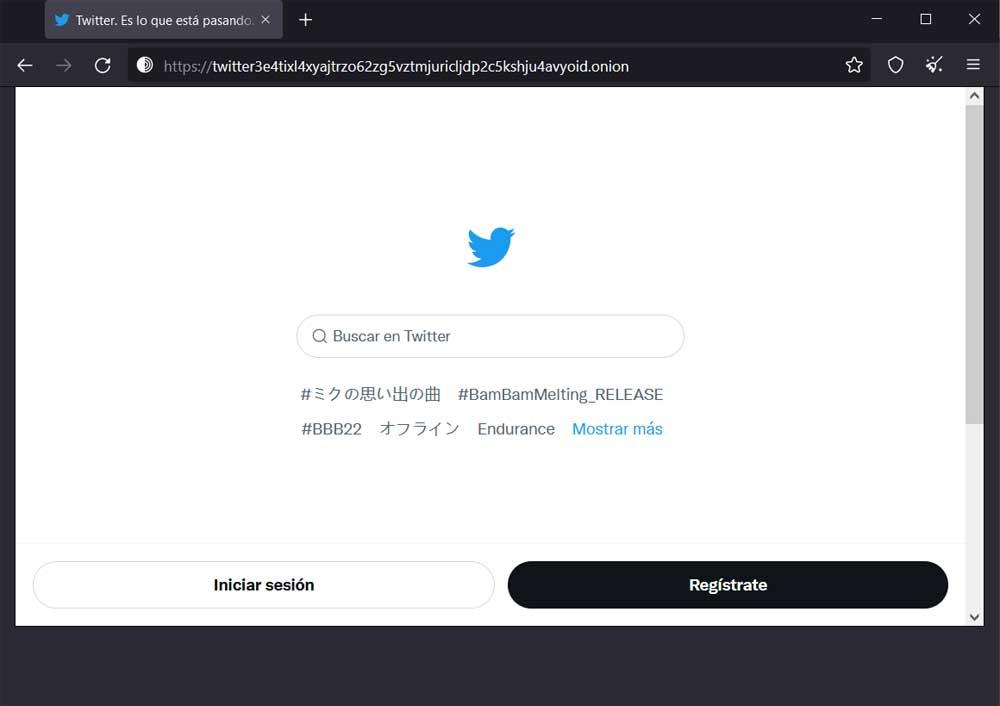
Enter the social network using Brave
As we mentioned before, we can also access the Tor network from the browser characterized by its privacy, brave. As in the previous case, all we have to do is download the corresponding executable and install it on our computer. Once it is up and running, by default, when trying to access a .onion website, we will see that the program gives us an error. But in the case at hand, to access the Twitter social network from here, all we have to do is click on the icon of the private network that appears in the address bar.
![]()
Once we have clicked on this icon we mention them, a new private window will open to make use of the onion addresses of the Tor network. Therefore, in what follows, we will only have to introduce the url commented before in the same address bar to be able to access the new Twitter website.
Among the advantages of using Twitter with one of these two programs using the private network, is that we do it through an .onion address. As a general rule, these improve the authenticity and availability of internet portals. Therefore, this movement guarantees us access to the correct site. At the same time, onion websites like this one prevent attacks made against them. In addition, we can bypass regional locks, we will have protection against DNS censorship or TLS man-in-the-middle attacks.












