If you have a D-Link DIR-605L Wi-Fi router, you should stop using it and buy another model as soon as possible, as a major security flaw has been detected that could affect your security, and the manufacturer will not update the firmware of this equipment because it has reached its end of useful life. In late December 2023, a security researcher informed the manufacturer about an authentication-related vulnerability, which could trigger incorrect access control and this router could be attacked from the router’s LAN. Do you want to know all the details of how this security flaw works?
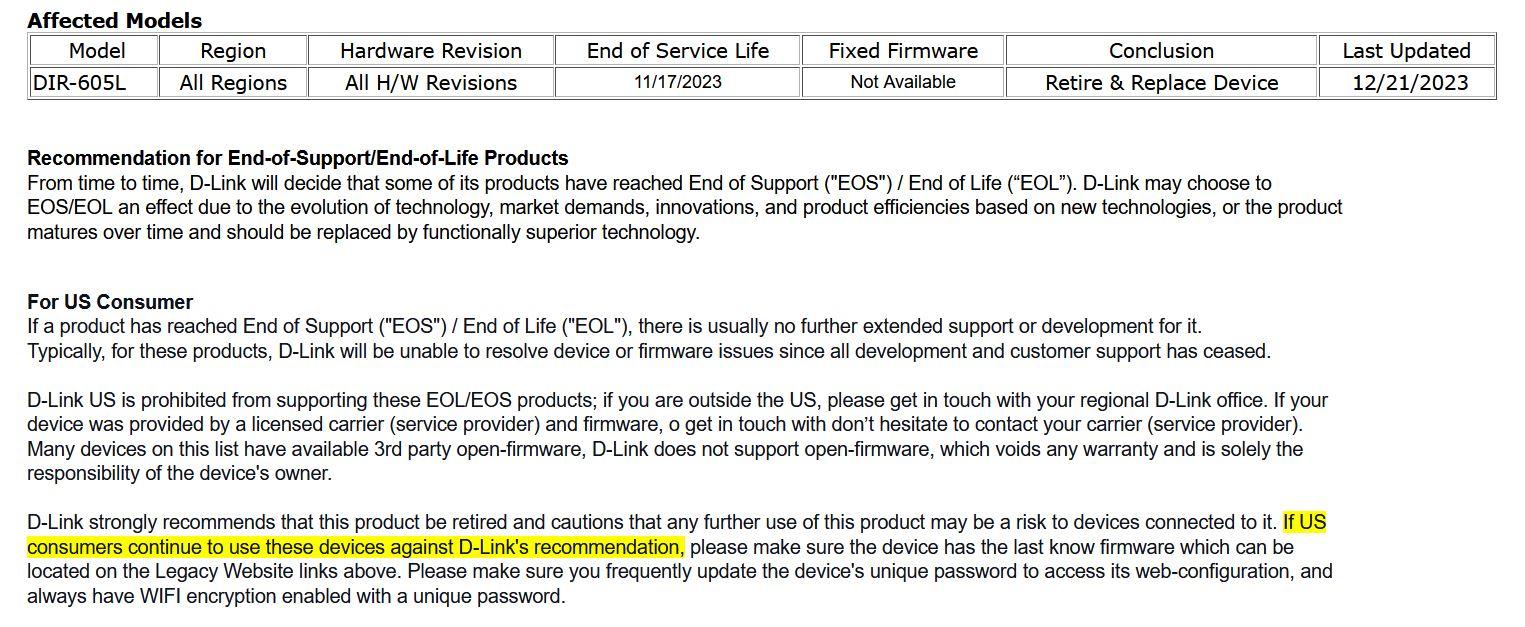
On December 20, 2023, the manufacturer was informed that there was a serious security flaw in its D-Link DIR-605L router, however, this equipment reached the end of its useful life just a month before, specifically on November 17, 2023. 2023. When a router from any manufacturer enters EOL (End of Life) it stops receiving software updates or security patches.
What does this security flaw consist of?
This vulnerability is that an authenticated user could trigger incorrect access control and elevate privileges in the local network (LAN and Wi-Fi). In addition, it is possible to exploit other router configurations by having permissions. as team administrator. The author of communicating the vulnerability to the manufacturer D-Link, has published on X (formerly Twitter) a video on how this router can be compromised, since he has programmed an exploit for this purpose:
Oscar Alfonso Diaz
@OscarAkaElvis
I finished the exploit for vulnerability I’ve found on the D-Link DIR-605L router (CVE-2023-51119).
I made a PoC video. I’ll send it to exploitDB tomorrow.
#hacking #cve #researching https://t.co/Uw4vKwqIxZJanuary 11, 2024 • 11:27
56
0
In the previous video you can see how the entire process is carried out with a router reset to factory settings. The first thing it will do is check that the “SessionHijacked” password does not work on the router, and returns an authentication error. So, after running the exploit you designed to exploit this vulnerability, you will be able to hijack the administrator user’s password very easily. For the exploit to work properly, there needs to be a legitimate administrator session, so we simply have to launch said exploit and wait for someone to log in and then it will be able to hijack the password.
What does D-Link recommend in this regard?
The manufacturer D-Link, through the technical support officer website where they make different announcements and statements, recommends that you do not use this D-Link DIR-605L router and replace it with any other, since this model has reached the end of its useful life and there will be no new firmwares patching this vulnerability that has been found . This policy is common in the industry, but keep in mind that this bug was found just a month after it reached the end of its useful life, and D-Link will not fix it for only one month, so the best is that you change it as soon as possible.
In the past, companies like Microsoft and their operating systems have stopped receiving security updates due to reaching the end of their useful life, but on certain occasions they have released important patches solving important vulnerabilities, to give their users time to update to a newer version. It seems that D-Link is adamant on this matter, and unfortunately there will be no updates.













