When browsing the web, you should also be aware of fraudulent websites out to steal your information. Fortunately, Safari on the iPhone and iPad has a so-called phishing filter that warns you when you visit a potentially fraudulent website. This also comes in handy, for example, when opening a link from a phishing email that seems to come from Apple, who are out to steal your Apple ID information.
- Enable Phishing Filter
- Glossary: what is phishing, spam malware etc?
How can I enable the phishing filter on iPhone?
The phishing filter warns you that a website may be dangerous even before you open the actual website. To enable these alerts, do the following:
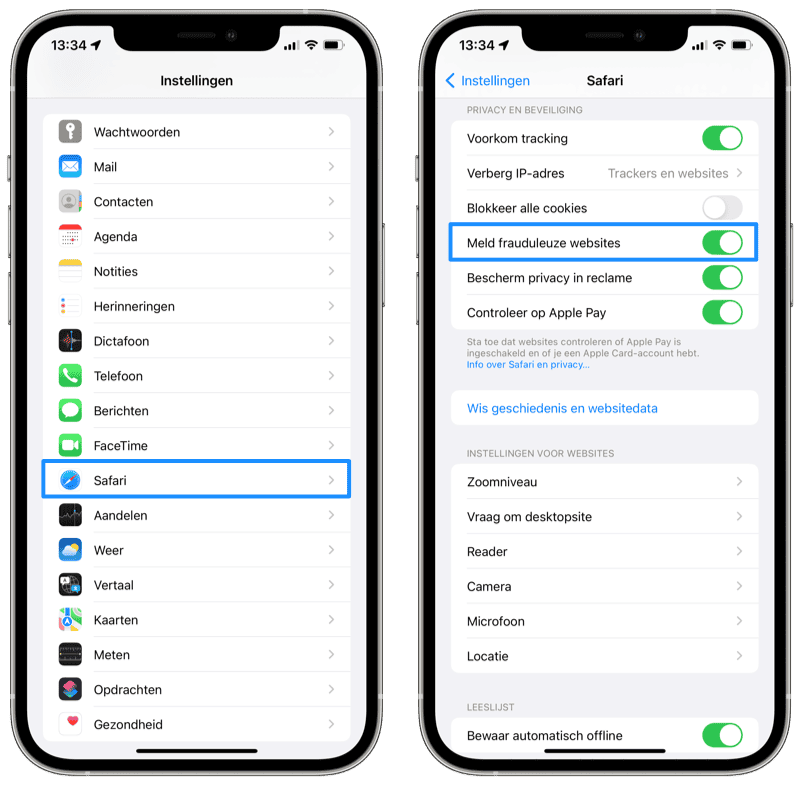
- Open the Settings app.
- Tap Safari and scroll to the Privacy and Security heading.
- Make sure the switch next to Report fraudulent websites is turned on.
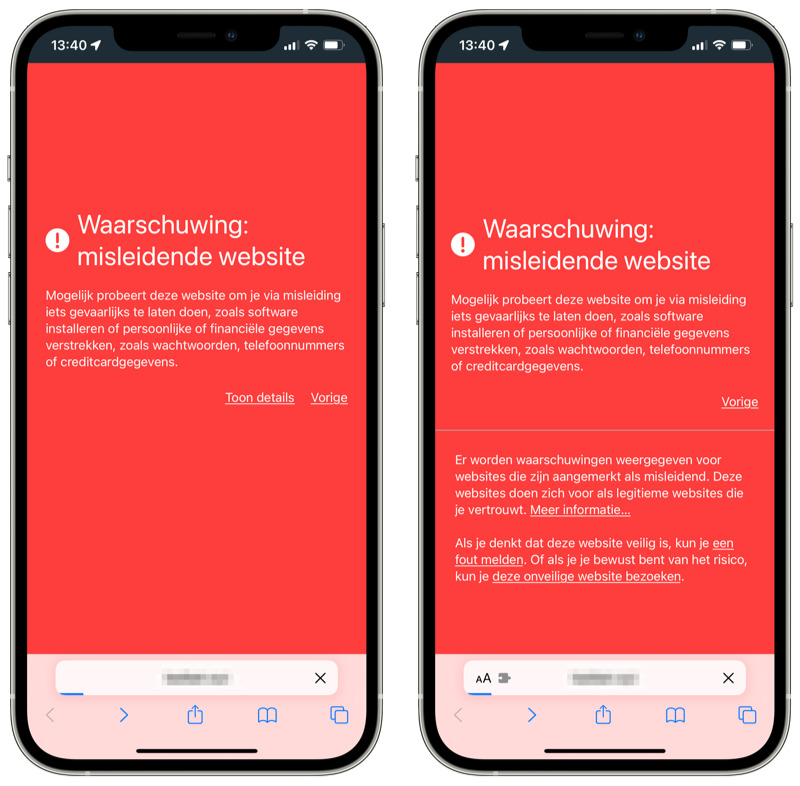
If this setting is enabled, you will receive a warning before the relevant site appears. The warning can be recognized by a red bar at the top of the screen and with the red text “Possible phishing website”. You can now choose the option Go back to return to the previous page. If you are sure that the website is legitimate and that it is NOT a phishing website, you can tap Ignore this warning.
On a website like phishtank.com you can consult a database of (possible) phishing websites. Safari will not warn you about every possible phishing website, but it will try to protect you as best it can.
What does phishing, spam and malware mean?
Not very familiar with the terms used in internet crime? This list will get you started!
-
Phishing: Online “fishing” for information such as passwords, account numbers and social security numbers, by sending spoofed emails or creating websites that are strikingly similar to those of institutions such as the police or banks.
-
Spam: Mass sending of e-mails without the consent of the recipients.
-
Malware: Collective term for malicious software, such as viruses, trojans, adware and bots.
-
Ransomware: A form of malware in which files on your computer are held hostage and are only released when you pay a ransom.
-
Keylogger: Program that keeps track of keystrokes someone makes. The data is sent to the hacker, who can use it to retrieve passwords. You can install a keylogger unnoticed via a Trojan horse.
-
Trojan horse: Program that piggybacks on other software and installs itself unnoticed on a PC. For example, a Trojan horse may contain a keylogger.
-
Botnet: Network of infected computers that are controlled from a central point, without the owners of the PCs knowing they are infected. A computer that is infected and forms part of a botnet is also called a ‘zombie’.
In our tip Recognizing phishing messages from ‘Apple’ you can read how to recognize phishing emails and pages that appear to come from Apple. This prevents Apple ID phishing or other information from your account information being passed on.