iPhone hacked? That way you know for sure
If a message ‘iPhone hacked’ (or variants thereof) appears on the screen, it does not always mean that someone has actually broken into your device. In many cases, these are fake messages that are out to steal your data (so-called phishing). These are intended to frighten you and ask you, for example, to click on a link to solve the problem. Never do this! There is a good chance that you will download malware, so that a malicious person can still take control of your phone. It is best to ignore these messages. But what to do if you suspect that your iPhone has been hacked? We discuss that in this article.
- Can an iPhone be hacked?
- Step-by-step plan for hacked iPhone
- Prevent a hacked iPhone
- Apple ID hacked
- Social media profile hacked
- iPhone camera or microphone hacked
Can an iPhone be hacked?
The simple answer to that is: yes. In general, you are better protected with an iPhone than with other devices, but you are never 100% safe. It is possible to hack an iPhone remotely, even without the intervention of the owner. So you don’t have to click on a link or install a malicious app.
The point is, however, that these types of attacks almost always target prominent people such as politicians, journalists, human rights activists and artists. Valuable information can be found with those people, for example nude photos that can be sold to the tabloid press or scandals about cheating, contacts with Russia or China and the like. The most notorious is the Pegasus software, with which the iPhones of journalists and politicians have been hacked. However, this is quite expensive software, which is mainly used by totalitarian regimes. The chance that you as an ordinary user will be affected by this is quite small: it is simply too expensive to apply en masse to many citizens and it does not provide enough valuable information. Mass surveillance of citizens in countries with an oppressive regime can of course occur and the massive collection of user data by companies such as Meta/Facebook does of course occur, but this often has a completely different approach.
However, even as an ordinary citizen you have to be on your guard. Investigation services can tap your phone and track your location, for example if you are associated with a crime while on holiday abroad. It is also quite possible for hackers to switch on your microphone and camera remotely. However, the biggest risk factor is you: by sharing your location and search behavior with all kinds of third-party services, they don’t need to have physical access to your iPhone to know where you’ve been and what you’re up to.
Step-by-step plan for hacked iPhone
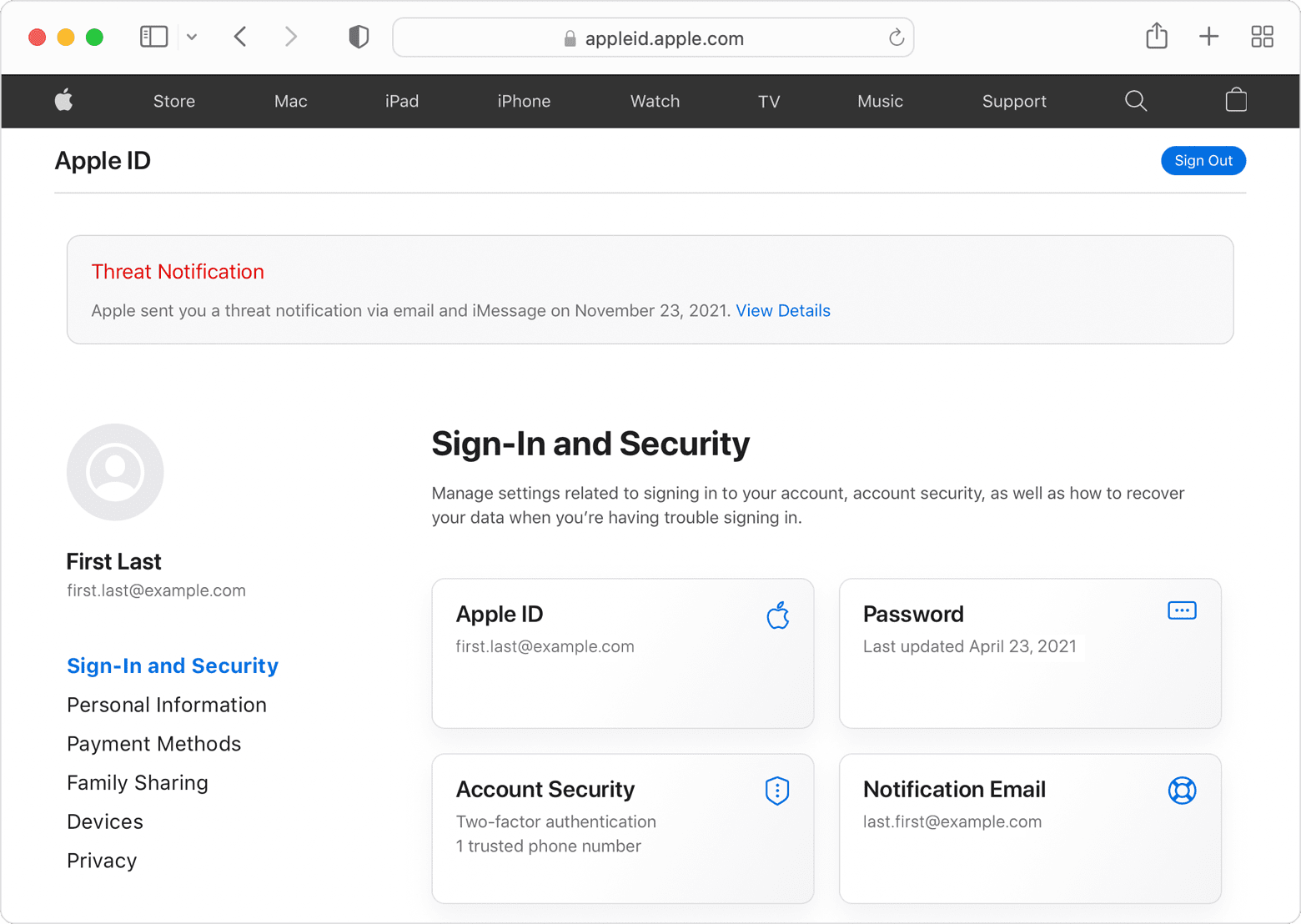
If your iPhone has actually been hacked, you can find more information on this Apple page. These are attacks carried out by, for example, authoritarian regimes. When Apple notices this, the following happens:
- A notification appears at the top of the appleid.apple.com page
- Apple sends an email and iMessage message to the email address and phone number associated with the Apple ID.
Apple recommends doing the following:
- Update to the latest software, as it often has security updates applied.
- Protect your device with an access code.
- Use two-factor authentication and a strong password for your Apple ID.
- Only install apps from the App Store.
- Use strong and unique passwords.
- Do not click on links and attachments from unknown channels.
As you can see, these recommendations are a mix to prevent hacking of hardware (your iPhone) and software (your Apple ID). Often this is mixed up.
Prevent a hacked iPhone
We can add the following:
- Use the iVerify tool to discover anomalies and abnormal situations in iOS. The tool also provides all kinds of tips to better secure your iPhone.
- Restart the iPhone. Any spy software running in the background can therefore be disabled. This does not always have to be spy software from a malicious regime, but it can also be a tool to monitor your doings (installed by a jealous partner, for example).
- Set a 6-digit or alphanumeric passcode, which is not easy to guess. So no logical sequences such as 123456, dates of birth (including those of your partner or children), the name of your pet or other easily guessable personal information.
- Do not connect to unsecured Wi-Fi networks.
- Watch for suspicious behavior, for example if you suspect SIM swapping. But don’t overdo it, because not every app that behaves strangely is proof that your iPhone has been hacked.
- Only use your own charger. There have been (rare) cases where malware has been installed via manipulated cables.
Apple ID hacked
As we mentioned above, hacking your (physical) iPhone and hacking your Apple ID sometimes get mixed up. It will not always be possible to penetrate your device to take over physical control. More often it involves hacking into your Apple ID and accounts, something separate from the tangible device.
With the Apple ID, a malicious person can download apps at your expense and modify your personal information. You can prevent this by setting up two-factor authentication for your Apple ID. A trusted device is then always required to log in. Because this is a physical device, it is quite difficult to perform a remote hack: after all, the attacker must be able to see what code appears on your screen.
Many of the tips we mentioned above, such as setting a hard-to-guess password and keeping your private information secure, also work to prevent your Apple ID from being hacked.
Social media profile hacked
The chance of being hacked is ultimately not that great with an iPhone, if you stick to the most important recommendations. What happens much more often is that social media profiles are hacked. Every year, this happens to about 2% of the Dutch population, according to the Cyber Security Monitor of Statistics Netherlands. Usually this is because people have set an easy-to-guess password or use the same password several times.
If such a password is involved in a data breach (for example from LinkedIn), it is easy for a malicious person to try the password with other services, such as Twitter or Instagram. That is why it is wise to also choose two-factor authentication for these services, especially for services that are important to you, that you use a lot or where you can incur a lot of damage, such as PayPal or Marktplaats. If your account has been hijacked, you can often report this on a special webpage of the relevant service. The account can then be temporarily inactive or ‘frozen’.
Here’s what you can do if your social media profile has been hacked:
- Temporarily set the account to private or inactive.
- Change password and enable two-factor authentication.
- Contact support to regain access to your account.
- Ensure that the linked e-mail address is properly secured, because this allows malicious parties to reset your account or change personal data.
More tips can be found here:
- This way you can see if someone has been in your Twitter account
- Has your Instagram account been hacked? This is how you get your account back

Can anyone hack iPhone camera and microphone?
You sometimes hear stories of people who just talked to a friend about a certain subject and were shown commercials on the same subject shortly afterwards. There is a suspicion that a company has been eavesdropping on you via the microphone, or even watched the conversation via the camera. It does not always mean that someone has indeed been peeping. Sometimes people reveal themselves through their behavior, for example by searching Google or by buying something online.
But it is (in theory) possible that the camera or microphone is switched on remotely without you noticing it. Normally there should be a light on the screen when the camera or microphone is active, but if there is a security vulnerability or if malware is active on your device, this could be disabled.
Here too, it is best to install iOS and app updates as soon as possible. Only use apps that you really need, so that you can see what the culprit could be in case of strange behavior. At Apple, a check has always been carried out in the App Store to check for malware, but even then something can slip through. If you use beta apps via TestFlight, there is less control over that.
If software wants to watch along with the camera or listen in via the microphone, it could also be called ‘stalkerware’. This is software that someone secretly installs on your device to monitor your behavior, for example in case of suspicion of adultery. You can pay attention to the following points:
- Check the App Library to see which apps have been installed recently and see if there’s an app you don’t recognize. Use Google to find out if this might be spyware or stalkerware.
- Check in Settings if there are apps that you don’t recognize.
- There is a trusted certificate that you have not installed yourself (can be found via Settings > General > Info.
- The screen of your iPhone remains active longer than usual or your device is slower.
- The battery suddenly drains faster than usual.
- A person from your environment behaves strangely and, for example, asks remarkably often to “look something up on your phone”.
If your battery drains faster, it’s not always caused by malware. It could also just be an app that hasn’t yet been optimized for the latest iOS version, or that runs unnoticed in the background. If you have few apps installed, it will also take less effort to find the culprit.
More tips about hacking can be found on the Dutch site Laatjeinethackmaken.nl. You will also find many more additional tips there, including about safe chatting and safe internet banking.














