We live in an increasingly digital world in which we are increasingly dependent on the Internet. We no longer store our personal and work information on paper and instead store it in files. Then to store our data we opt for the cloud or our own equipment. Cybercriminals look for ways to profit from our information and one of the most profitable is ransomware attacks. In Spain we are increasingly immersed in the transition to the digital world and it shows. In this article we are going to see how ransomware attacks in Spain are becoming important.
Why ransomware is increasing in Spain
The way of working in Spain has changed a lot in recent years and this has undoubtedly accelerated the transformation to the digital world. Although it is true that there are quite a few countries like the United States that are more advanced than us. Cybercriminals are launching ransomware attacks that aim to encrypt our files and then ask us to pay a ransom.

In this aspect, a worrying fact is that almost a third of the victims of ransomware in Spain paid the ransom. However, there are several reasons why we should not pay a ransomware ransom, one of which is that we are incentivizing this type of crime to increase. On the other hand, in Spain due to the COVID pandemic we have seen how, as in many other countries, remote work has increased. This has caused changes in our legislation such as the approval of the remote work law.
How ransomware affects different countries
An AtlasVPN report based on Cyberint research on ransomware attacks in 2021 found that 48% targeted the United States. On the other hand, among the most threatened sectors were the industrial and energy businesses, retail trade and finance. In this investigation, it is already seen how the problem of ransomware in Spain is beginning to be important, although it is quite far from the top positions. This is a graph with the TOP 10 countries in terms of ransomware cases.
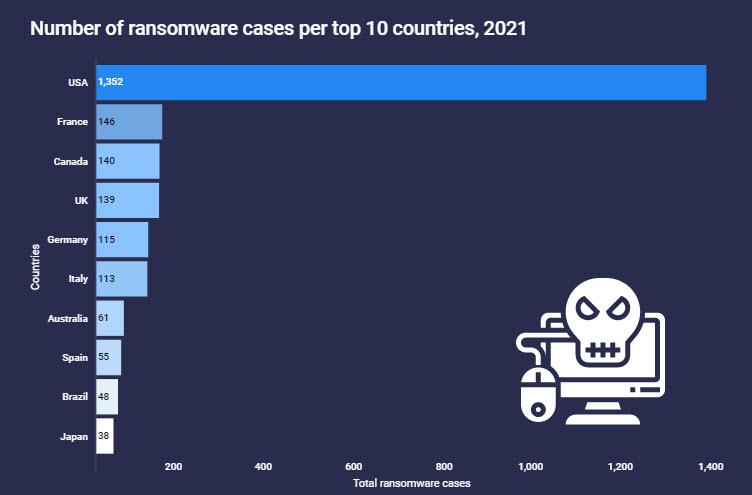
In 2021 there were 2,845 ransomware attacks of which a number that reached almost half with 1,352 affected the United States. There the attacks on Colonial Pipeline, JBS Foods and Kaseya were famous. Next comes another major group with over 130 attacks. Here the first European country appears, France with 146 attacks, followed by other countries such as Canada with 140 and the United Kingdom with 139. In the next countries that exceed 100 attacks would be Germany with 115 and Italy with 113.
Then would come the group that concerns us, that of those over 50, here would be Australia with 61 and in terms of ransomware in Spain it would be 55 attacks. Finally, with about 40 attacks, Brazil and Japan will close the TOP 10 list.
Sectors most affected by ransomware
As for the targets of the hacking groups, they targeted very large companies because their shutdown caused more damage. Thus, some of them decided to pay a ransom to get back to work as quickly as possible without affecting more people and losing as little reputation as possible. Here, we have a chart showing how ransomware cases affected the industry.
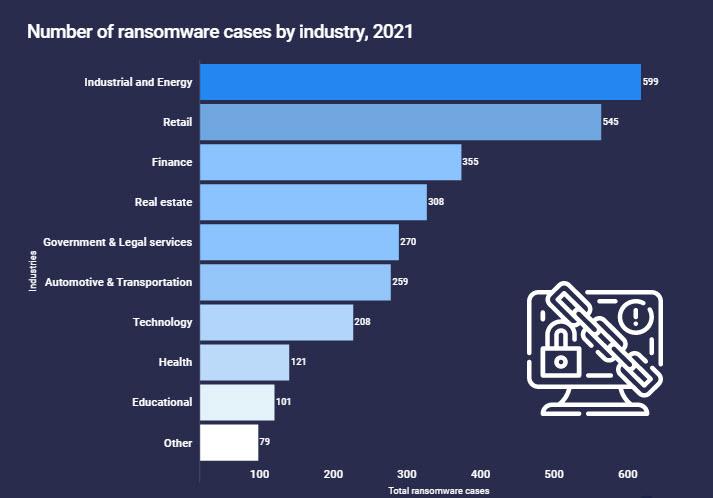
Looking at the data by sector, we find that energy and industrial organizations suffered 599 ransomware attacks. Furthermore, cybercriminals targeted companies in the retail industry in 545 attacks last year. In that regard, hackers targeted retailers when they are most vulnerable, such as during the Black Friday or Christmas sales seasons. You have to remember that at this time is where they make a large part of the year’s sales. Lastly, we have the financial industry which experienced 355 ransomware attacks as they are seen as offering potential targets with high payment opportunities.
What to do to avoid being a victim of ransomware?
The first thing you should do to avoid being a victim of ransomware and losing all your files is to make backup copies following the 3-2-1 scheme, this means that you should do the following:
- Make a total of 3 backups.
- 2 backup copies on different media, not on the same PC or server where we have everything.
- 1 backup that is offline, that is, an external hard drive that is not permanently connected to the computer.
You can also use services like pCloud that provide us with 2TB of cloud storage with the possibility of going back if the files are encrypted, of course, any other cloud storage service that allows us this functionality would also be very valid. The best thing you can do are local backups but also in the cloud, any precaution is not enough.
Once we have a good backup policy in place, you will need to do the following if you use a computer:
- Having an antimalware or antivirus on our PC, most ransomware is easily detected by these software.
- Have Windows anti-ransomware functionality enabled. In case of detecting the typical behavior of a ransomware, it will try to block it so that it stops encrypting our files.
In the case of having a NAS server, it is highly advisable to perform the following actions:
- Cut off any external access to the NAS (from the Internet), except the port used by the VPN server, either OpenVPN or WireGuard.
- Disable the default “admin” account of our NAS server.
- Protect the administrator account with two-factor authentication.
- Configure notifications by Telegram, email or Push notifications of accesses and access attempts to our NAS server or services.
- Establish a backup policy in the cloud or to another properly configured NAS server.
As you can see, with some basic security recommendations and a lot of common sense when it comes to opening executables or downloading things from the Internet, we can be protected against these attacks.













