WiFi connections have an encryption that allows us to be protected when connecting to the Internet and that you have surely seen when setting up a network. This encryption can be of several different types and has been advancing as time has passed or technologies have improved. Surely you have heard of WEP, WAP, WAP2, WPA3… we see them in most routers, devices with WiFi and adapters and they allow us to prevent unauthorized users from obtaining personal information or using our connection for illicit purposes. For this reason, the types of encryption exist since the end of the nineties.
There are various types of encryption and most current routers and WLAN adapters support the latest versions but you may have an outdated device that is not capable of supporting WPA2 or WPA3 for example.
encryption types
At first, WiFi networks were protected by the WEP standard, ‘Wired Equivalent Privacy’, which despite its name was shown to not provide the security of a wired network. With specific software, and in just two minutes, it was easy to bypass this WiFi network protection system. Then came WPA, and if its first version only lasted a year, it is because it was also quickly shown that it was not secure, or not as secure as intended.
WEP
WEP stands for Wired Equivalent Privacy, as we have explained in the previous paragraph. A wired privacy system that arrived in 1997 with the intention of becoming an option to protect us when using wireless networks. The initial idea of WEP was to encrypt the data so that it could not be read if it was encrypted. But there were many problems and the main one we have explained in the introduction. It only took a few minutes to decipher this data.
WEP was responsible for encrypting the traffic with a static key that could be a 64-bit key with 10 hexadecimal digits or a 128-bit key with 26 hexadecimal digits. The idea was correct: avoid attacks. But it was not achieved since it had serious flaws and vulnerabilities that allowed anyone to get this data. So much so that in 2004 the WiFi Alliance officially withdrew WEP as a mechanism or type of security for WiFi connections.
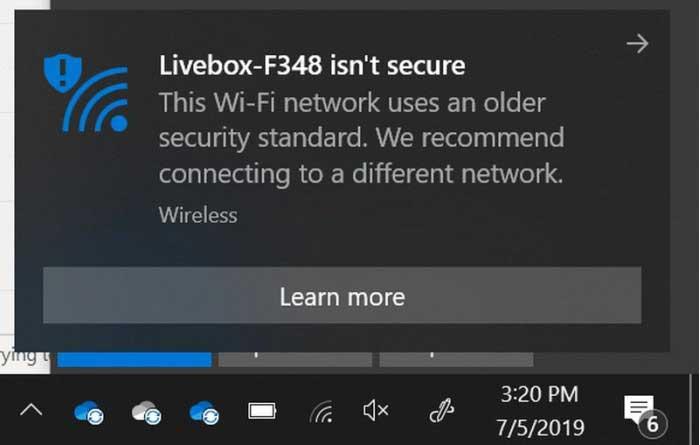
Currently using WEP is totally inadvisable and is considered an obsolete type of security. It was replaced in 2003 by WPA, which sought to remedy these security problems and inconveniences that had been found. In fact, Windows 10 confirmed in 2019 that it would prevent users from connecting to networks that use WEP or TKIP as encryption since its May 2019 Update. As we collected in ADSLZone, a message appears indicating: “XXX is not secure. This Wi-Fi network uses an old security standard. We recommend that you connect to another network»
WPA
WPA or WiFi Protected Access (that is, protected WiFi access) was the replacement for WEP to avoid vulnerabilities and lack of security. It was released in 2003 by the WiFi Alliance and offered improvements. The main one is the use of a temporary key integrity protocol as opposed to WEP providing the same key to each authorized system. It is known as TKIP or Temporal Key Integrity Protocol that allows the key used by systems to be changed dynamically. It was more secure than WEP, but it is not totally secure today and it is not used either.
In other words, WPA was a change and an improvement over WEP, but it was not the definitive change since it was still weak and still had vulnerabilities. Encryption was better, and dynamic, self-distributing keys helped, but in 2004 the WiFi Alliance introduced WPA2 with one big change: the use of the AES Advanced Encryption Standard for encryption.
WPA2
This new version was created to correct the bugs and deficiencies of the WPA system and was released in 2004, just one year after the system it serves as an evolution. It uses the AES encryption algorithm (Advanced Encryption Standard) and is suitable for both the private and public sectors.
Its progress implies greater security when accessing data, either through a password or through access to a server. This system was in force for more than a decade, but in the end a vulnerability was found and an evolution was created, the WPA3.
WPA3
This security protocol strengthens encryption to prevent malicious access to a person’s data when using a Wi-Fi network. And it does so using 192-bit encryption versus 128 for its predecessors, making it more difficult to bypass that encryption chain and access the data you want to protect.
It protects weak passwords better, because it is less vulnerable to a brute force attack. This is the current protocol, increasingly implemented, and the one that offers greater robustness against attacks and data theft attempts.

WPA2 vs WPA3, differences and changes
With the WPA2 standard, one of the easiest to execute was the brute force attack, based on a dictionary attack. That is, take the key record that associates an SSID with its password, based on the various models of routers and other access points, and try generic passwords. This is one type of attack, but it’s the conventional brute force attack, constantly trying random keys until it hits the right one. This is more complicated with WPA3, as described by Kevin Robinson, vice president of marketing for the Wi-Fi Alliance, while the authentication process is one of the main improvements: it is more complicated and requires much more time to try, since each key requires interaction with the WiFi network.
Once access to the WiFi network has been gained in an unauthorized way – or yes, but for questionable purposes – there is another important security improvement. On the WPA2 standard, communications on a Wi-Fi network are encrypted, but with 128-bit keys as the maximum length. Now, with the arrival of WPA3, the main difference is that these communication encryption keys extend up to 192 bits. That is to say, that there are longer chains and therefore with more complex combinations –to understand it more simply-, then it is remarkably more complicated for someone to spy on the content of the communications between a device and its access point, using WiFi.

However, this point is configuration dependent. Just as on WPA2 the 128-bit encryption keys marked an optional maximum, this happens with the 192 bits in WPA3; that is, the network will have to be configured to use 192-bit keys, and therefore maintain the maximum possible security in communications.












