Bad news for the thousands of users who use certain models of Android TV decos sold throughout the world. According to the Dr. Web team of professionals, a new version of a dangerous Trojan has been discovered that is infecting these devices. Unfortunately, as we are going to tell you, getting infected with this virus is quite simple.
In 2015, a Trojan known as Pandora became very popular, breaking down the defenses of all kinds of devices so that hackers could use them at will. Over time it was found with countermeasures and lost popularity. Unfortunately, according to what the Dr. Web security team says on your websitePandora is back with a new version.
Attacks against cheap decos
There is one thing in common that all Android TV set-top boxes that have been affected by this malware have: they are cheap models. These are the ones that usually add up to thousands and thousands of sales on pages like AliExpress or Amazon, devices that are sold cheap and that are usually the ones we jump into because they offer good value for money. Because it is already known that, in many cases, we do not need anything too pompous to watch television and use other applications.

Some of the models that have been affected are the following: H96 Max X3, MX10 Pro 6K and Tanix TX6 TV Box, but they are not the only ones. We are not going to link to them for obvious reasons, but if you take a look in the Amazon catalog you will have no problem finding them. Therefore, it is important that you check that it is not the deco that you are using in your day to day. In addition to being cheap models, there is another factor in which they agree: all these decos include a quad-core processor that enables hackers the possibility of carrying out DDoS attacks.
How infection occurs?
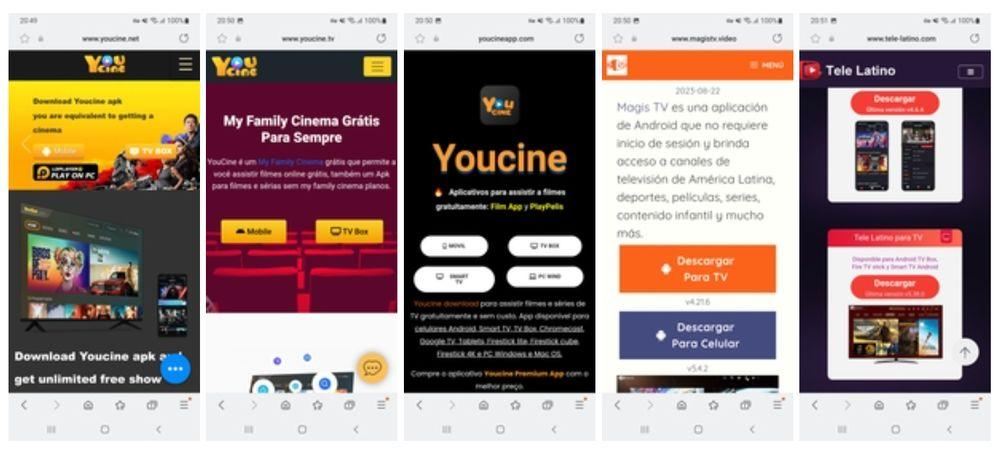
Unfortunately, getting infected is not as complicated as one might wish. This virus can enter decos in different ways. The most common is through applications that are downloaded and installed on the device from pages dedicated to piracy. It is already known that all these types of downloads are dangerous, since the exposure to viruses or problems is constant. After all, you never know what can come “as a gift” with the app you are installing. In this case, Pandora is getting into many decos from pirate websites like the ones you can see in the image.
Another way of infection is falling for a fake firmware update that can make you think you have to update your deco when, in reality, there is no new version available. All that supposed update does is introduce the malware to your computer, leaving it open to hackers who want to abuse the device. In some cases, firmware updates are presented on some web pages as a way to get access to unlimited content or features that are not normally available to you. They are usually messages like “update your firmware with this trick and you will see unlimited movies”. Other times it is promised that, by updating the firmware from that website, your deco will be compatible with more apps and services. The promises and tricks that hackers use are varied, so there are many ways to fall for their traps.
In other cases, and this is really dangerous, the Trojan itself comes “as standard” with the device if you bought it from a reseller who is camouflaging viruses to benefit hackers. The problem with these Android decos is that they are usually marketed by independent vendors and not directly by manufacturers, so the risk exposure is high. Therefore, it never hurts to check the profile of the sellers before making the purchase.
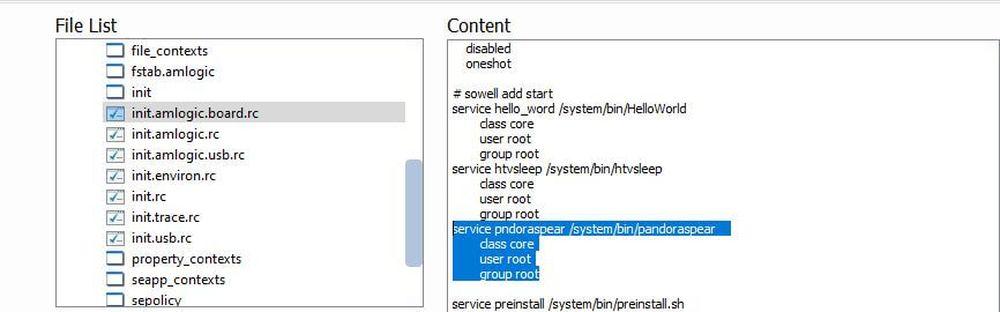
The infection process, once the malware has slipped into the deco, is practically instantaneous. And as they say from Dr. Web, it is a persistent threat. The user is unaware of what is going on behind their backs when the GoMediaService system is enabled to run automatically at device startup. After this, that tool unpacks the virus and runs several files that lead to Pandora establishing itself inside the system with the “.tmp.sh” file. From then on, the virus stays in standby mode so that hackers can remotely control your device by performing all kinds of actions that you may not even be aware of.













