A report recently published online reveals that more than 86,000 routers have been exposed to various security problems that have left them completely exposed. The incident has occurred in a large number of countries, which also includes Spain.
Vulnerabilities in routers are not something new. There are already several occasions on which, throughout the year, we have talked about incidents that have put different network terminals at risk. This time the report in question comes from Forescout Vedere Labs, who has published a very extensive dossier talking about the problems that Sierra Wireless brand routers are suffering.
Highly threatened routers
One of the problems with this discovery is that the routers that are at risk have not been exposed to reduced risk. The truth is that a wide series of vulnerabilities that these OT/IoT teams are facing are detailed.
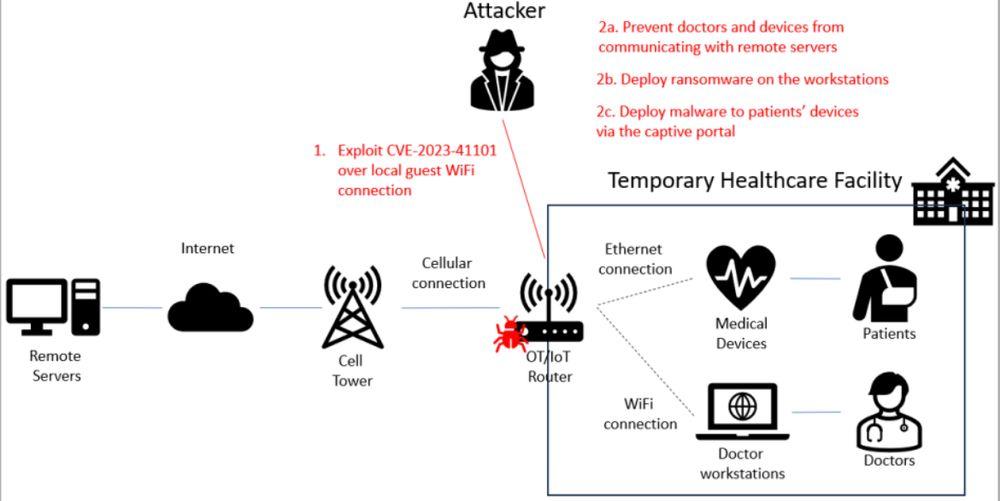
Attackers can, for example, bypass authentication processes, perform unauthorized access, execute code remotely, use cross-site scripting, or carry out other attacks, such as denial of service. The good news is that these Sierra Wireless routers are not typically used in the home, but the bad news is that they have more important functions and uses. For example, they are routers that are used in different emergency services, in government office systems, in organizations dedicated to health, in factories, power plants or in other types of equally sensitive places. Therefore, the fact that there is a security risk means that it should be taken seriously.
These are the vulnerabilities discovered
The models affected in the security incident are AirLink, a type of router that is highly rated due to the great performance it provides. The Sierra Wireless company is well known throughout the world and also has a notable presence in our country, so the name is surely familiar to many of the specialists who work with this type of routers. In particular, they are devices that tend to be recurring in relation to 5G connections and the establishment of WiFi networks that provide stability between different terminals.
The Forescout report refers to the fact that the vulnerabilities discovered affect both routers and several specific components, including OpenNDS and TinyXML. Of the total problems analyzed, one of them has been classified as having a critical risk level, eight have a high risk and the rest are established at medium or low levels.
The highest risk vulnerability is known as CVE-2023-41101, which allows remote code execution in OpenDNS and reaches a danger score of 9.6. With a little less risk, a similar vulnerability called CVE-2023-38316 has been detected, while others registered include CVE-2023-40463, which provides unauthorized access in ALEOS, or CVE-2023-40458, which allows make a denial of service attack. In any case, the complete list of the 21 vulnerabilities can be seen at the report you published Forescout and you will surely be interested in consulting the specialists who work with this type of routers on a daily basis.
The security firm recommends taking action quickly, since they have detected more than 86,000 affected routers and, in some cases, hackers can use these weaknesses to launch botnet attacks. The good news about what happened is that the majority of the routers at risk are in the United States, although equipment in Spain has also been affected, as can be seen in the heat map that has been published within the study.
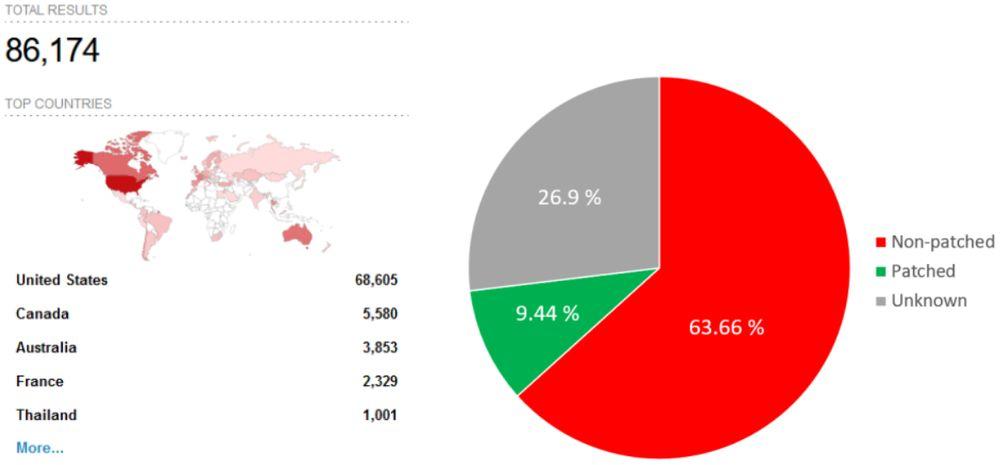
The solution that has been provided along with the publication of the report is for administrators to update the routers to version 4.17.0, given that there is already a solution and patch for all the vulnerabilities. And it would be something to carry out as soon as possible, since although some of these vulnerabilities had already been detected some time ago, it has been found that only a handful of thousands of routers have been patched to avoid them. Maybe it would be time to take it seriously before some regrettable incident occurs.














