Different types of malware are always lurking to enter our computers and infect them. For example, a new type of virus was recently discovered that disguised itself as Google Translate or other programs to download Mp3 music, which basically installed itself on computers in order to mine cryptocurrencies from infected PCs.
And it is that, the digital world has both good and bad things. One of them is the various fake apps that are distributed through various legitimate freeware stores until they are found to harbor malware and removed. For this reason, we will always have to be very careful about what we finally install on our computers.
The program that hides the malware
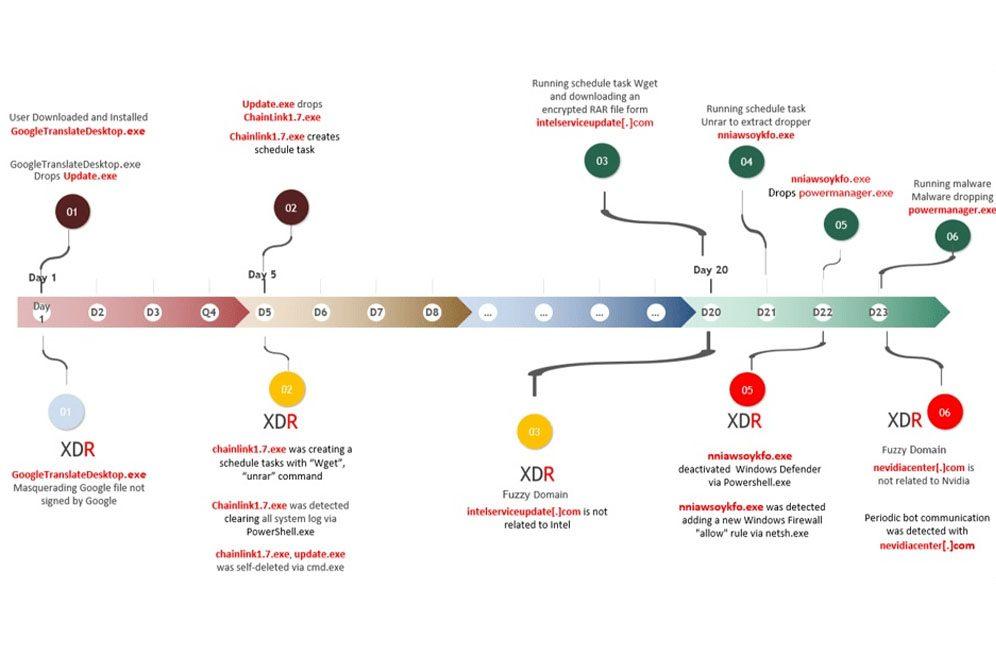
This particular virus has been recently discovered by Check Point Research. In their research, they have made it clear how this particular malware works. Basically, according to their report, the virus has been created by a developer named ‘Nitrokod’. At first, the program that it installs on the computer seems to be free of malware and allows us to use it with the function that it promised us.
However, the problem starts to appear a month after the program is installed on the computer. More than anything, because the software has the objective of deliberately delaying the installation of the different malware components until a month later in order to avoid being detected by the different antiviruses that users may have. At that time, the virus managed to mine cryptocurrencies without the victim realizing it.
In total, it has achieved more than 111,000 victims in up to 11 countries since 2019: the United Kingdom, the United States, Sri Lanka, Greece, Israel, Germany, Turkey, Cyprus, Australia, Mongolia and Poland. Furthermore, this type of malware has found its way onto popular sites like Softpedia and Uptodown. The programs used to trick users were services that do not have a desktop application for PC: Yandex Translate, Microsoft Translate, YouTube Music, MP3 Download Manager and Pc Auto Shutdown.
How does this virus work?
And it is that, regardless of the program that had been downloaded (with the signature of this developer), the user who wanted to install it, received a password-protected .rar file in which they found an executable with the name of the application. Once it was executed on the computer, a four-stage countdown was started in which the necessary components were installed for the malware to be completely installed.
This was achieved by the fact that, after execution, the software triggered a dropper of another encrypted .rar file obtained via Wget on the fifth day of infection. Finally, once the virus was complete, a connection was established to a remote command and control (C2) server where a configuration file was retrieved to start mining cryptocurrencies on the infected PC.
Therefore, the only way to protect ourselves from this type of malware is to avoid downloading different software that the original developer has not officially released, as has been the case with Google Translate. In this way, we can avoid falling into the trap of this type of developer.