In the last few hours, it has become known that a group of Russian hackers, who exclusively stalked Ukrainian entities, have begun to launch hacking attacks on users around the world through a USB worm that spreads silently. , without us hardly realizing it. If you want to know which group of cybercriminals it is, we offer you all the information in the following lines.
Massive attacks by hackers on organizations in other countries are the order of the day and are one of the most problematic events of the 21st century. Without going any further, Spain is one of the countries that receives the highest number of cyber attacks globally, ranking seventh, with a percentage of 3%, according to cybersecurity experts S21sec.
In this context, Russian hackers, who a few months ago began sending cyber attacks to the Ukrainian authorities, have begun to spread throughout the world, accompanied by a USB worm that includes very powerful malware that spreads from one computer to another. very effective way.
Russian USB worm spreads
Since the Russian-Ukrainian war, numerous altercations have occurred that remain unresolved today. So much so that Russia has begun to launch cyberattacks in recent months on Ukrainian companies thanks to access to powerful ransomware tools. But not content with that, Russian hackers have started a global threat that threatens users around the world.
This is the LitterDrifter group, a very dangerous team of cybercriminals whose main mission is to spread a malicious worm through a USB that is transferred to other units automatically, assuming command of the command and control servers. However, this group encompasses other well-known names such as Gamaredon, Primitive Bear, ACTINIUM, Armageddon and Shuckworm and emerged in 2014.
Consequently, researchers from the company Check Point have seen “indications of a possible infection in other countries such as the United States, Hong Kong, Vietnam, Chile, Poland and Germany, so all this indicates that LitterDrifter has spread more beyond its intended objectives. However, experts say that this number of infections may be approximately half of those that directly affect Ukrainian organizations.
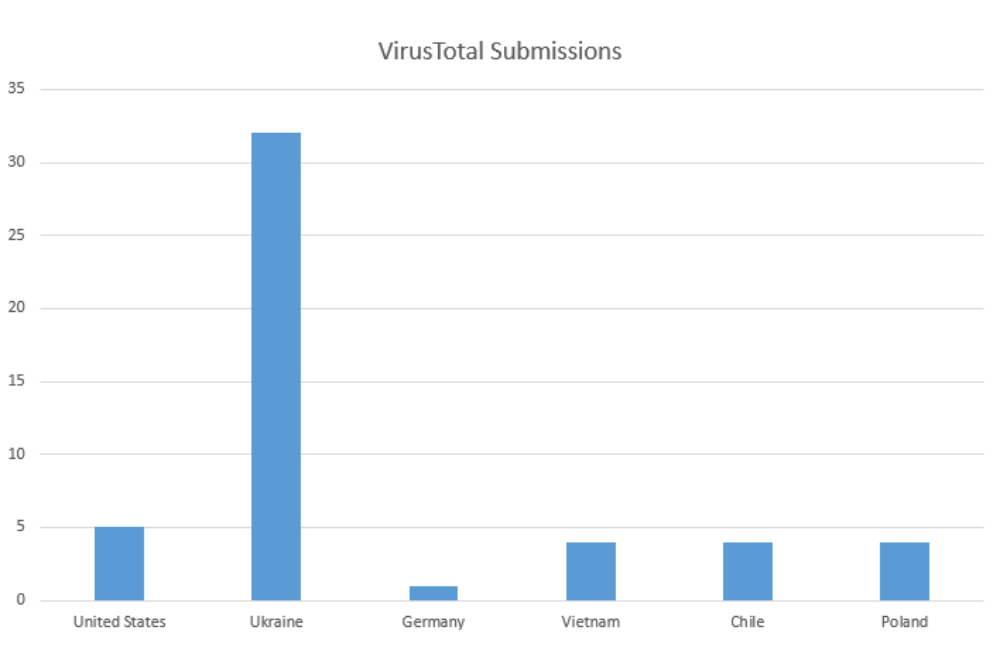
How Russian malware affects
The main purpose of LitterDrifter is to penetrate the command and control (C&C) server and distribute the malware via USB drives to other systems. Next, domains are established as a placeholder for the IP addresses where the command and control server is located. Apparently, although they are not new, their techniques are quite effective and can corrupt files on a much larger scale. Hence its large-scale spread.
Therefore, the use of its methods has turned this malware into a maximum security alert worldwide, since it can guarantee the expansion of much broader objectives and cause a catastrophe of gigantic dimensions.














