Connecting to a free WiFi network is a lottery. Sometimes we do it out of desperation, because we have no other option to turn to if we want to send a message, consult a map or look for any kind of thing. But perhaps, by doing so, we are getting into a problem. Luckily, a new tool developed by security experts ensures that you can identify dangerous networks. So you will not expose yourself to a threat again.
The work that security researcher and specialist Tom Neaves has done has been superb. He has put himself in the position of users, of those who do not have great knowledge in technology, WiFi or security, to design a tool that allows them to avoid problems. He has christened her Snappy and, in no time, she has been received in style.
WiFi network problems
As Neaves mentions in the diary he has published about the work he has carried out, the main problem with WiFi access points that are scattered around the world for free is that they are not analyzed enough. A user connects to the WiFi connection at his favorite coffee shop, and when he returns the next day, he reconnects to his wireless network because he already knows it works. But what if he is no longer connecting to the same network?

That is the problem that the expert raises and that he wanted to solve. As he says, it’s really easy for hackers to find popular WiFi networks and duplicate them so that users connect to them thinking they’re safe. In a very simple way they can create a fake WiFi access point that has the same name. But they can still go further and copy the MAC address of the connection so that it is practically impossible for the user to know that they are not connecting to where they think they are connecting.
snappy is the solution
Once he had confirmed what the big security problem was, Neaves got to work to develop a solution that could warn users that they were connecting to a different network than the original one they had been connected to days before. . At the same time, he also considered that if he was going to create a program like this, he would also give it the ability to detect the use of airbase-ng, which is the most widely used tool for hackers who attack by creating fake access points. Connection.
With that in mind, he began looking for static data that would always be bound to a connection, since that way he could create a “signature” for each access point. In the end, after evaluating many parameters, he came to the conclusion that the best data to use were some such as BSSID, maximum power transmission rate, Max_A_MSDU, the channel or the country, to name just a few. From there, he would establish a rule in his tool under which all access points matching this data would be trusted, while those with changed items would be suspect and not worth using.
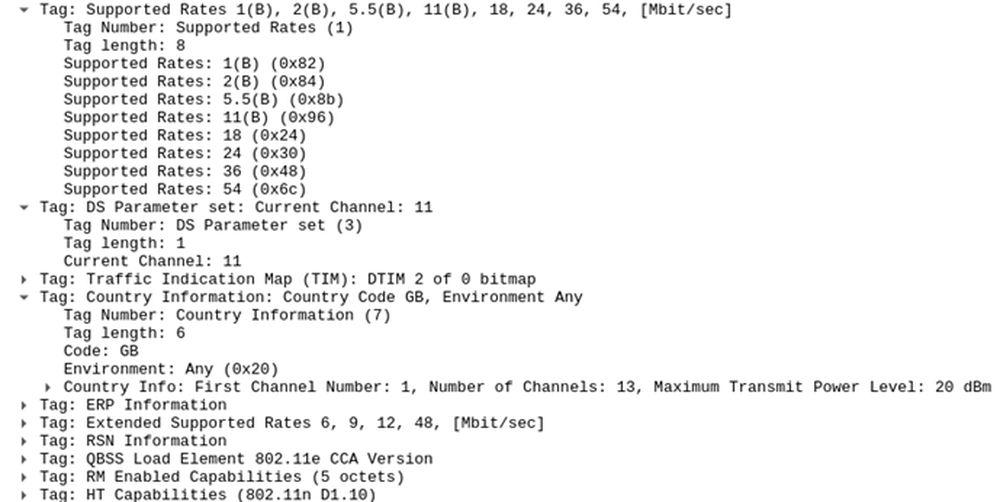
Having determined this, he went to work, turning the idea into a tool known as snap.py (Snappy) that runs on Python and is available on GitHub. That brings us to the next point: the way in which we can use it.
How to use Snappi?
Nowadays, you need to use Python, so it’s not as easy as just downloading a mobile app. You will have to download the tool and use it on a computer with Python or on mobile devices through specialized applications. If you have an Android phone, it would be best to download Pydroid 3while in the case of iOS users they have alternatives such as Pythonista 3 which also work without any problem.
When you load the tool that you have to download from GitHub by following the link that we have left you before, you will have the opportunity to use it and analyze the networks. What Snappy (hence its name) is all about is taking a snapshot of the networks you connect to, and then when you come back, you compare it to the current state of the access point. The system will inform you if it is the same connection or not, so you know that you can connect or if it would be better not to. It also works by detecting fake and dangerous networks with code hints that will let you know, for example, that you’ve come across an airbase-ng based network.
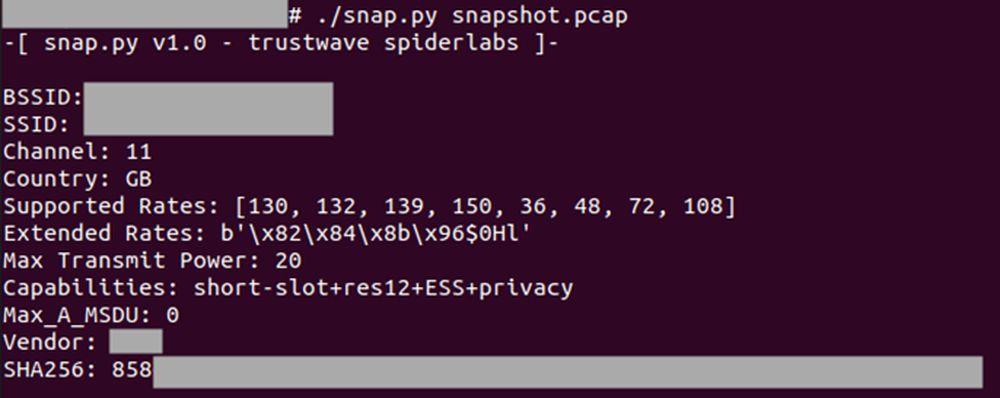
It is important that you know that you can use Snappy both online and offline, so if you are short of data and have no option to connect, you don’t have to worry. After all, that is what it is about: knowing if the available WiFi network is trustworthy or not. Of course, if the use of this tool seems very complicated, since resorting to Python is not the most common in the day-to-day of users, it is possible that its function ends up turning into an application that is easier to use.
We will have to wait to see what are the plans that Tom Neaves has in this regard. What is clear is that it can be a very useful tool to check that the WiFi in hotels, shops, shopping centers or restaurants is safe.














